반응형

VPC란?
참조 : https://monta010.tistory.com/30
1. Custom VPC 생성
provider "aws"{
region = "ap-northeast-2"
}
resource "aws_vpc" "vpc-0-0-0-0" {
cidr_block = "10.0.0.0/16"
instance_tenancy = "default"
enable_dns_hostnames = true
tags = {
Name = "vpc-0-0-0-0"
}
}

2. Public Subnet 및 Private Subnet 생성
resource "aws_vpc" "vpc-10-0-0-0" {
cidr_block = "10.0.0.0/16"
instance_tenancy = "default"
enable_dns_hostnames = true
tags = {
Name = "vpc-10-0-0-0"
}
}
#Public IP 1번
resource "aws_subnet" "subnet-pub1-10-0-1-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
cidr_block = "10.0.1.0/24"
availability_zone = "ap-northeast-2a"
#EC2 생성시 퍼블릭 자동 할당
map_public_ip_on_launch = true
tags = {
Name = "subnet-pub1-10-0-1-0"
}
}
#Public IP 2번
resource "aws_subnet" "subnet-pub2-10-0-2-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
cidr_block = "10.0.2.0/24"
availability_zone = "ap-northeast-2c"
#EC2 생성시 퍼블릭 자동 할당
map_public_ip_on_launch = true
tags = {
Name = "subnet-pub1-10-0-2-0"
}
}
#Private IP 1번
resource "aws_subnet" "subnet-pri1-10-0-3-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
cidr_block = "10.0.3.0/24"
availability_zone = "ap-northeast-2a"
tags = {
Name = "subnet-pub1-10-0-3-0"
}
}
#Private IP 2번
resource "aws_subnet" "subnet-pri2-10-0-4-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
cidr_block = "10.0.4.0/24"
availability_zone = "ap-northeast-2c"
tags = {
Name = "subnet-pub1-10-0-4-0"
}
}

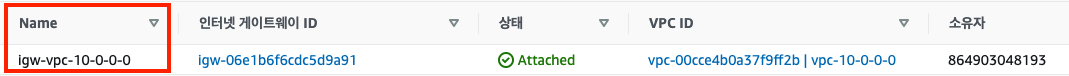
3. Internet GateWay 생성
#InterGateWay
resource "aws_internet_gateway" "igw-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
tags = {
Name = "igw-vpc-10-0-0-0"
}
}
4. Route table 생성 및 associate(VPC 연결)
- public 라우팅 테이블 생성 및 라우팅 테이블에 VPC연결
#라우팅 테이블
resource "aws_route_table" "rt-pub-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw-vpc-10-0-0-0.id
}
tags = {
Name = "rt-pub-vpc-10-0-0-0"
}
}
#라우팅 테이블 -> VPC 연결
resource "aws_route_table_association" "rt-pub-as1-vpc-10-0-0-0" {
subnet_id = aws_subnet.subnet-pub1-10-0-1-0.id
route_table_id = aws_route_table.rt-pub-vpc-10-0-0-0.id
}
resource "aws_route_table_association" "rt-pub-as2-vpc-10-0-0-0" {
subnet_id = aws_subnet.subnet-pub2-10-0-2-0.id
route_table_id = aws_route_table.rt-pub-vpc-10-0-0-0.id
}
- Private 라우팅 테이블 생성 및 라우팅 테이블에 VPC연결
#라우팅 테이블 생성_Private
resource "aws_route_table" "rt-pri1-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
tags = {
Name = "rt-pri1-vpc-10-0-0-0"
}
}
resource "aws_route_table" "rt-pri2-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
tags = {
Name = "rt-pri2-vpc-10-0-0-0"
}
}
#라우팅 테이블 연결_Private
resource "aws_route_table_association" "rt-pri1-as1-vpc-10-0-0-0" {
subnet_id = aws_subnet.subnet-pri1-10-0-3-0.id
route_table_id = aws_route_table.rt-pri1-vpc-10-0-0-0.id
}
resource "aws_route_table_association" "rt-pri2-as2-vpc-10-0-0-0" {
subnet_id = aws_subnet.subnet-pri2-10-0-4-0.id
route_table_id = aws_route_table.rt-pri2-vpc-10-0-0-0.id
}
5. Elastic IP 및 NAT Gateway 생성
5.1) Elastic IP 생성
#EIP IP 생성(nat-2a)
resource "aws_eip" "nat-2a" {
vpc = true
}
#EIP IP 생성(nat-2c)
resource "aws_eip" "nat-2c" {
vpc = true
}
5.2) NAT GateWay
#NAT GateWay (Public-2a)
resource "aws_nat_gateway" "natgw-2a" {
allocation_id = aws_eip.nat-2a.id
subnet_id = aws_subnet.subnet-pub1-10-0-1-0.id
tags = {
Name = "gw NAT-2a"
}
}
#NAT GateWay (Public-2c)
resource "aws_nat_gateway" "natgw-2c" {
allocation_id = aws_eip.nat-2c.id
subnet_id = aws_subnet.subnet-pub2-10-0-2-0.id
tags = {
Name = "gw NAT-2c"
}
}5.3) 라우팅 테이블(Private)
- Private 라우팅 테이블에 모든 트래픽(0.0.0.0/0)을 NAT GW 전달하도록 설정
- 해당 Private Zone에 있는 대상은 모든 NAT를 통해서 외부 통신
#라우팅 테이블(Private) -> NATGateWay-2a
resource "aws_route_table" "rt-pri1-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_nat_gateway.natgw-2a.id
}
tags = {
Name = "rt-pri1-vpc-10-0-0-0"
}
}
#라우팅 테이블(Private) -> NATGateWay-2c
resource "aws_route_table" "rt-pri2-vpc-10-0-0-0" {
vpc_id = aws_vpc.vpc-10-0-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_nat_gateway.natgw-2c.id
}
tags = {
Name = "rt-pri2-vpc-10-0-0-0"
}
}
6. EC2 생성
6.1) Bastion(중계서버) 1대, Private-EC2 2대
- Private EC 2대를 통해 ALB 테스트
resource "aws_instance" "bastion" {
ami = "ami-0a0de518b1fc4524c"
instance_type = "t2.micro"
#key_name = "tf-key-pair"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2a"
subnet_id = aws_subnet.subnet-pub1-10-0-1-0.id
root_block_device {
volume_size = 30
volume_type = "gp2"
}
tags = {
Name = "bastion"
}
}
resource "aws_instance" "web-2a" {
ami = "ami-0a0de518b1fc4524c"
instance_type = "t2.micro"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2a"
subnet_id = aws_subnet.subnet-pri1-10-0-3-0.id
root_block_device {
volume_size = 30
volume_type = "gp2"
}
tags = {
Name = "web-2a"
}
}
resource "aws_instance" "web-2c" {
ami = "ami-0a0de518b1fc4524c"
instance_type = "t2.micro"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2c"
subnet_id = aws_subnet.subnet-pri2-10-0-4-0.id
root_block_device {
volume_size = 30
volume_type = "gp2"
}
tags = {
Name = "web-2c"
}
}
7. Application Load Balancer 생성
#AWS Security-Group#
resource "aws_security_group" "alb-sg" {
name = "alb-sg"
description = "alb-sg inbound traffic"
vpc_id = aws_vpc.vpc-10-0-0-0.id
ingress {
description = "TLS from VPC"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "alb-sg"
}
}
#AWS ALB#
resource "aws_lb" "web-alb" {
name = "web-alb" #ALB Name
internal = false #인터넷용
load_balancer_type = "application" #Application
security_groups = [aws_security_group.alb-sg.id] #security Name
subnets = [aws_subnet.subnet-pub1-10-0-1-0.id,aws_subnet.subnet-pub2-10-0-2-0.id]
enable_deletion_protection = false #ALB 삭제 보호
tags = {
Name = "web-alb"
}
}
#AWS Target-Group#
resource "aws_lb_target_group" "web-alb-tg" {
name = "web-alb-tg"
port = 80
protocol = "HTTP"
vpc_id = aws_vpc.vpc-10-0-0-0.id
health_check {
enabled = true
healthy_threshold = 3
interval = 5
matcher = "200"
path = "/"
port = "traffic-port"
protocol = "HTTP"
timeout = 2
unhealthy_threshold = 2
}
}
#Listner
resource "aws_lb_listener" "web-alb-ln" { ##Listener Name
load_balancer_arn = aws_lb.web-alb.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.web-alb-tg.arn
}
}
#Listner Target_group
resource "aws_lb_target_group_attachment" "foreach" {
for_each = toset(data.aws_instances.test.ids)
target_group_arn = aws_lb_target_group.web-alb-tg.arn
target_id = each.key
port = 80
}
data "aws_instances" "test" {
filter {
name = "tag:Name"
values = ["web-*"]
}
}
#DNS_NAME 출력
output "alb-dns_name"{
value = aws_lb.web-alb.dns_name
}7.1) Application Load Balancer Test
ALB DNS Name : alb-dns_name 를 통해 ALB 테스트



8. Amazon Machine Image(AMI) 생성
- 생성된 EC2를 AMI 생성
#Provider : AWS , Region
provider "aws"{
region = "ap-northeast-2"
}
# 인스턴스 정보 불러오기
# Tag Name 기준으로 web-* 모든 것들을 불러옴)
data "aws_instances" "test" {
filter {
name = "tag:Name"
values = ["web-*"]
}
}
#인스턴스 정보 불러와서 for_each 문을 통해서 반복하여 AMI 생성
#web-* 생성된 EC2만큼 생성됨
resource "aws_ami_from_instance" "instance_ami" {
for_each = toset(data.aws_instances.test.ids)
name = each.value
source_instance_id = each.value
tags = {
Name = "web-${each.key}"
}
}- 생성 완료
- web-<Instance_id>

반응형
'Terrform' 카테고리의 다른 글
| [terraform] terraform module( VPC) 사용 (0) | 2024.11.13 |
|---|---|
| AWS Terraform tfstate 파일 원격 관리(S3, DynamoDB) (0) | 2024.11.11 |
| Terraform Application Load Balancer(ALB)생성 (0) | 2021.08.02 |
| Terraform EC2 생성 (0) | 2021.08.02 |
| Terraform 정의 (0) | 2021.07.28 |




댓글